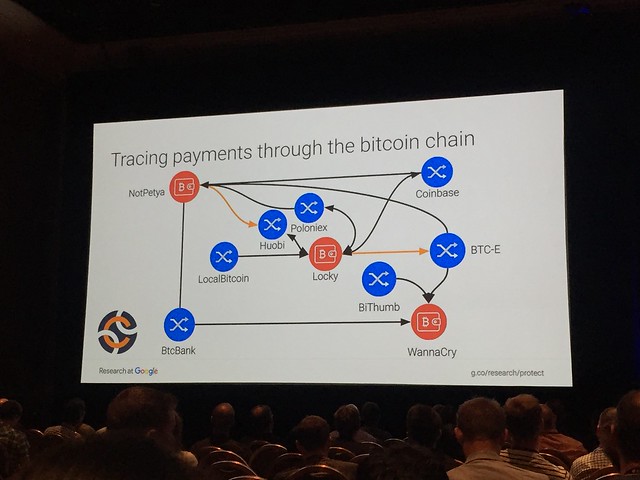
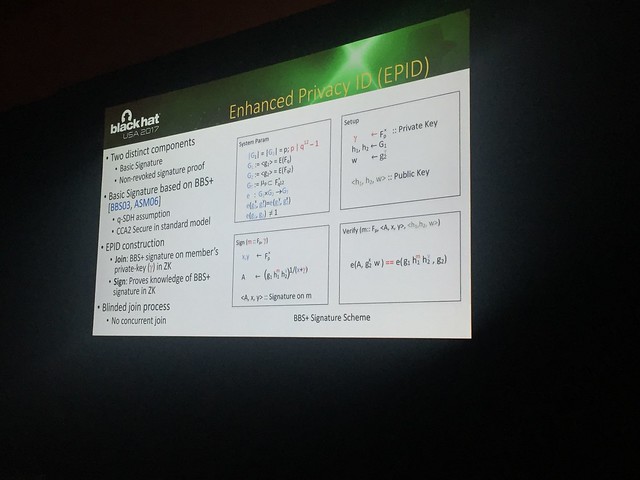
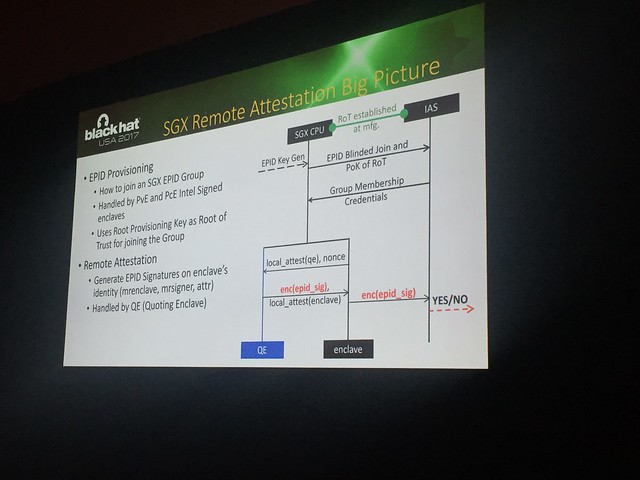
BlackHat/DefCon founder, Jeff Moss! Lots of lasers! This is
the twentieth year for BlackHat – incredible (and I’ve only been twice, though
many more times to DefCon, starting with DefCon 2). There are attendees from over 80 countries
and over 200 scholarship recipients.
The first year’s speakers were basically all of Jeff’s
friends – he just wanted to know what they were working on. People say that if
hackers and security researchers are talking about a problem now, it will be a
problem for the rest of us in 6 months or a year. It’s a “crystal ball” of
computer security. He learned in the
first year to never hold a BlackHat in the same hotel as DefCon – otherwise the
DefCon attendees come early and eat all of your food and drink all of you
booze! DefCon is more of a hacking conference – a creative way to explore.
Moss found the Internet to be quite liberating as a 13 year
old boy – he could go online and discuss things like rock and roll and nobody
knew he was just a kid. It took him awhile to fully understand, but he’s
learned the importance of being social. Your future success will be based on
how social you are. How much money can
you spend on defense and protecting the systems? Sounds technical, but to get
budget needed, it’s really a social and political conversation to do defense
greater than offence.
Security is no longer a local problem – it is a global
problem, though the problems vary by geo. Issues faced in Palo Alto are different
than those being faced in Bangalore or on a remote island.
We have to get engaged in the problems of lack of diversity
and lack of generalists – mentor, help people write CFPs, advise upcoming
students, get out there and help.
Alex Stamos, CSO, Facebook. Twenty years ago he couldn’t
afford BlackHat, but he was at DefCon and he found a place where he belonged.
Coming to the desert every year and hanging out with DarkTangent (Jeff Moss) is
like a reunion. Coming together as a group now for weddings, birthdays and baby
showers. In 2002, he brought his then girlfriend to BlackHat for their first
vacation – she’s been with him every years since.
Attending and speaking at DefCon and BlackHat is not always
safe for people for their career or livelihood. For example, one man quit his
job on stage so he could discuss router vulnerabilities, another engineer was
arrested in the airport, others have had federal injunctions against them to
prevent them speaking. But this work is
important and impactful, and we need to share.
Nowadays people finally understand why they need to build
secure systems – no longer a fringe idea. We are no longer the ‘hacker kids’ –
we are CSOs, working for the federal government, and industry experts.
Many people in this room got into security well before they
were paid for it – on bbs’es, in hacker meetings and saving up summer job money
to come to Vegas for DefCon. The things we are talking about now will become
startups over the next 2 years – yet, we are not living up to our
potential. We are finding problems, but
we need to think about what we do after we discover bugs. We have to realize
how many people depend on the technology.
We have a tendency to focus on the complexity, not harm
caused. Adversaries will do the simpliest thing they can to exploit a
technology. It is fun to see really complicated attacks that someone worked
really hard to figure out – but that’s unlikely where the actual abuse will be.
Abuse is the technically correct use of technology to cause harm. This can
include exploitation of adults and children – can be done very easily, not
through complicated attacks.
We are suffering from lack of empathy. Think about the
expression of the problem being behind the keyboard – that attitude helps you
shift responsibility away from actually securing a system to an uninformed
user. “Just use your knowledge of X.503
to decide if this certificate is safe to use” “don’t click on that link” “don’t
use that site w/out HTTPS". We have
to understand there are more and more people coming online that don’t have
experience on the Internet and they need to be safe.
We have a problem with security nihilism – that we are all
under attack by the most sophisticated adversaries possible, any security that
doesn’t use encryption is “security through obscurity”.
About 10 years ago, there was a bunch of research on
technologies that are deployed in the cloud. The research on GPUS and
hypervisors was great – and made the public cloud more safe. This gave the
impression, though, that the public cloud was not safe, that the existing protections
were not good enough – those weren’t the real problems. The real problems were
excessive privileges, poorly defined network policies – things that are much
easier to address and to exploit.
We don’t want to discourage people to deploy any security features
just because they are not perfect – they are better than nothing and need to
help the bulk of users.
There is another fallacy where attackers believe they are
just as smart or smarter than people who design the systems, which is not
necessarily the case. Systems are designed under all kinds of constraints and
nobody is perfect.
Stamos feels strongly that people have a right to secure and
private communications, even though some people (law enforcement) don’t always
agree.
Think about people who have to try to put pedophiles and
people that exploit children behind bars. How can we help them, without
creating backdoors? How can we relate to and understand their needs?
At Facebook, they have a dedicated red team that all they do
is try to break into their systems – unannounced the blue teams. Stamos and Facebook are big proponents of bug
bounties – particularly for open source that everyone uses, but don’t
necessarily have big owners.
Millions of people are getting inexpensive smart phones that
are shipping with out of date operating systems – it’s still Facebook’s
responsibility to make sure their app is still secure on these devices. They
are worth protecting.
We also have to worry about protecting users during
elections – there are many issues (slide font too small to read), but we need
to think about what we can help with and what we can do.
The Belfer Center is working on a project to help protect
future elections from outside influence. Facebook is sponsoring this effort. In
November of next year, there will be many house seats, senate seats,
gubernatorial campaigns and local offices participating in elections. All of
these campaigns are built up from scratch from a technology point of view,
often with volunteers. How we can we help them build secure systems, easily? If
things go wrong, can we help them with mitigation and analysis? It needs to be
a practical solution – to do this, we must work as a team and we need to have
diverse teams. You wouldn’t want a toolbox with only the best screwdrivers in
the world, would you?
Facebook is sponsoring legitimate CTF competitions in middle
and high schools. The winner are treated like athletes – this is important to
increase interest in this field. Make sure your team is open and respectful of
discussing diversity. Be open to criticism, do not assume how a minority wants
to be treated. But remember, don’t make
snide comments, don’t ask women if they are here with their boyfriend – that
has impact. Be respectful. Things are
getting worse, not better. Let’s make this a special week here in Vagas this
week to be respectful of other people – if you see something that isn’t right,
call people out. This is a critical
moment – we’ve been asking for people to pay attention to us – now they are,
and let’s show them something great.